Difference between revisions of "Ntopng"
From HackerNet
Helikopter (talk | contribs) m (→Installation) |
Helikopter (talk | contribs) m (→Listener Port) |
||
| Line 10: | Line 10: | ||
=== Listener Port === | === Listener Port === | ||
| − | auto eth1 | + | echo "auto eth1" | sudo tee -a /etc/network/interfaces |
| − | iface eth1 inet manual | + | echo "iface eth1 inet manual" | sudo tee -a /etc/network/interfaces |
=== Portspegling === | === Portspegling === | ||
Revision as of 15:09, 10 May 2015
High-Speed Web-based Traffic Analysis and Flow Collection.
Contents
Installation
wget http://www.nmon.net/apt-stable/14.04/all/apt-ntop.deb && sudo dpkg -i apt-ntop.deb sudo apt-get clean all && sudo apt-get update && sudo apt-get -y install ntopng ntopng-data nbox sudo service apache2 restart
https://<IP>
credentials: nbox:nbox
ntopng konfas och startas från webgui:t
Listener Port
echo "auto eth1" | sudo tee -a /etc/network/interfaces echo "iface eth1 inet manual" | sudo tee -a /etc/network/interfaces
Portspegling
Det finns olika sätt att få den speglade trafiken till ntop.
vSwitch
Promiscuous mode
dvSwitch
Distributed Port Mirroring
Fysisk switch
RSPAN/ERSPAN
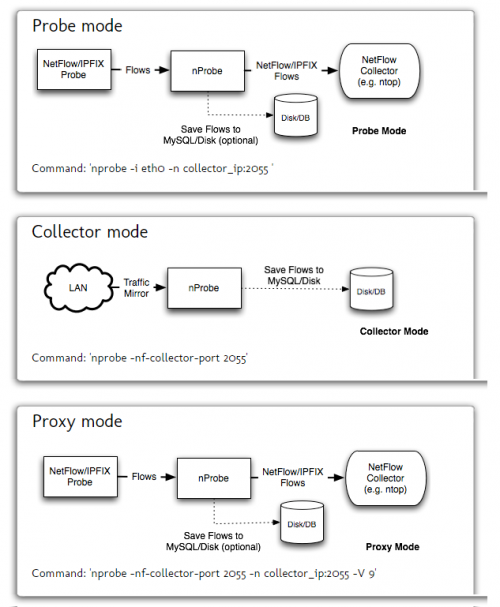
ntopng as Flow Collector
In ntopng flows are collected through nProbe that act as probe/proxy. The communication between nProbe and ntopng happens though ZeroMQ that decouples ntopng from nProbe.
OBS nprobe kräver licens
sudo nprobe --zmq "tcp://*:5556" -i none [eth0] -n none --collector-port 2055 & sudo ntopng -i tcp://127.0.0.1:5556